Cybersecurity Frameworks for Protecting Supply Chain Intellectual Property
The Criticality of Supply Chain IP Protection

Intellectual Property Protection in Global Supply Chains
Protecting intellectual property (IP) within a global supply chain is paramount to maintaining a competitive edge and safeguarding innovation. Companies often rely on intricate networks of suppliers, manufacturers, and distributors, each potentially possessing access to sensitive information about new products, processes, or technologies. Without robust IP protection strategies, this information could easily leak, leading to lost market share and financial damage.
Effective IP protection measures necessitate a proactive approach, encompassing clear licensing agreements, confidentiality agreements, and rigorous security protocols to safeguard proprietary data. Thorough due diligence on potential partners and suppliers is also crucial to identify and mitigate potential IP risks.
The Role of Licensing and Agreements
Licensing agreements play a vital role in defining the permissible use of intellectual property within the supply chain. These agreements should clearly delineate the rights and responsibilities of all parties involved, specifying the scope of permitted use, limitations, and compensation for the use of protected material. This legal framework is essential to prevent unauthorized use and ensure that all parties understand their obligations.
Furthermore, robust confidentiality agreements are critical to protect sensitive information shared among supply chain partners. These agreements should outline the specific information covered, the duration of confidentiality, and the consequences of breach. Implementing these agreements effectively is crucial to maintaining the integrity of the IP within the supply chain.
Protecting Trade Secrets in a Global Context
Protecting trade secrets is an essential component of a comprehensive IP strategy in a global supply chain. The complexity of international collaborations often makes it challenging to maintain control over proprietary information. Strong legal frameworks are needed to address the potential risks associated with disclosing confidential information to foreign partners.
Security Protocols and Data Protection
Implementing robust security protocols is crucial for safeguarding sensitive data throughout the supply chain. This includes establishing secure communication channels, employing encryption technologies, and regularly reviewing and updating security measures. This proactive approach protects the confidentiality of trade secrets and other proprietary information.
Regular security audits and training programs for employees involved in the supply chain are vital to ensure that everyone understands the importance of data protection and adheres to established protocols. These measures significantly reduce the risk of data breaches and unauthorized access.
The Impact of IP Infringement on Supply Chains
IP infringement can have significant consequences for companies involved in global supply chains. This can manifest in lost revenue, damaged reputation, and legal battles. The cost of IP infringement extends beyond the immediate financial losses and can compromise the long-term sustainability of a company. It's crucial for companies to proactively address IP risks and establish strong legal frameworks to protect their intellectual property assets within their supply chains.
Companies that fail to address these issues can face severe repercussions, potentially leading to a complete disruption of their supply chain operations and a loss of trust among stakeholders. Therefore, a robust IP protection strategy is not just a legal requirement, but a critical element for long-term success.
Implementing a Multi-Layered Security Approach
Layered Security Architecture
Implementing a multi-layered security architecture is crucial for safeguarding sensitive data and systems from a diverse range of threats. This approach involves establishing multiple defense mechanisms at different points within the infrastructure, effectively creating a layered defense. Each layer acts as a separate security checkpoint, increasing the overall resilience and reducing the impact of potential breaches.
A robust multi-layered security architecture is not just about adding more security tools, but rather about strategically combining various controls to create a cohesive and effective security posture. This integrated approach is more potent than relying on a single, isolated security measure.
Network Security
Network security forms the foundational layer of a multi-layered approach. This encompasses measures like firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to control network traffic, identify malicious activities, and block unauthorized access. Implementing robust network segmentation further enhances security by isolating sensitive data and resources.
Controlling network access through strong authentication and authorization policies is essential. This prevents unauthorized individuals from accessing sensitive data and resources within the network.
Endpoint Security
Endpoint security focuses on securing individual devices like computers, laptops, and mobile phones. This includes antivirus software, anti-malware programs, and endpoint detection and response (EDR) tools to detect and mitigate threats at the device level. Regular software updates and patching are critical components of endpoint security.
Strong password policies and multi-factor authentication (MFA) are essential for protecting endpoints from unauthorized access. Implementing these measures can significantly reduce the risk of successful attacks targeting individual devices.
Data Security
Data security measures protect sensitive data throughout its lifecycle, from storage and transmission to processing and use. This includes encryption, access controls, data loss prevention (DLP) systems, and secure data storage solutions. Data masking and tokenization are crucial for protecting sensitive data in transit and at rest.
Data encryption is a fundamental component of data security and should be applied to all sensitive data, both in transit and at rest. Regular data backups and recovery procedures are essential for mitigating the impact of data breaches or loss.
Application Security
Application security focuses on protecting applications from vulnerabilities and attacks. This involves rigorous testing for vulnerabilities during the development lifecycle, secure coding practices, and web application firewalls (WAFs). Regular penetration testing and security audits are critical for identifying and addressing potential weaknesses.
User Access Management
User access management (UAM) is critical for controlling access to resources and data. This involves implementing strong authentication and authorization mechanisms, as well as robust user provisioning and de-provisioning procedures. Regular user access reviews and audits are essential for maintaining appropriate access privileges.
Implementing the principle of least privilege is critical for minimizing the impact of potential breaches. This means granting users only the necessary access to perform their job duties.
Security Awareness Training
Security awareness training plays a vital role in educating employees about potential threats and best practices for security. This training should cover topics such as phishing scams, social engineering, password security, and data protection. Regular training updates are essential to keep pace with evolving threats and best practices.
Empowering employees with the knowledge and skills to recognize and report potential security threats is an important component of a strong security posture. This proactive approach can significantly reduce the risk of successful attacks.
Vendor Risk Management and Due Diligence
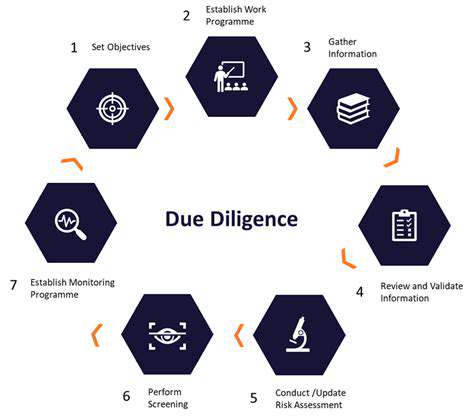
Understanding Vendor Risk Management
Vendor risk management (VRM) is a critical process for organizations to identify, assess, and mitigate risks associated with their third-party vendors. This process is vital for protecting sensitive data, maintaining operational continuity, and avoiding reputational damage. Effective VRM programs help organizations proactively address potential threats, such as financial instability, legal issues, or compliance violations, that could negatively impact their business. By understanding these risks, organizations can implement appropriate controls and safeguards.
A comprehensive vendor risk management program involves several key steps, including identifying all vendors, assessing their risks, and implementing mitigation strategies. This proactive approach helps organizations to minimize the potential impact of vendor failures and maintain a strong security posture.
The Importance of Due Diligence
Due diligence is a crucial component of vendor risk management. It involves a thorough investigation of a potential vendor to understand their capabilities, financial stability, and compliance posture. Thorough due diligence helps organizations make informed decisions about which vendors to partner with. This process can involve reviewing financial statements, assessing legal history, and examining compliance records. This investigation allows organizations to identify potential red flags and make informed decisions about whether to proceed with a vendor relationship.
Due diligence is not a one-time event; it should be an ongoing process. Regular reviews of vendors' performance and compliance are essential to maintain a strong vendor risk management program.
Identifying Potential Risks
A significant aspect of vendor risk management is identifying potential risks associated with each vendor. This involves evaluating various factors, including financial stability, regulatory compliance, security posture, and operational capacity. These factors can directly affect an organization's ability to maintain its operations and protect its assets.
Understanding the specific risks associated with each vendor is essential for developing targeted mitigation strategies. Identifying these vulnerabilities in advance is crucial for preventing potential disruptions and financial losses. Careful analysis of these risks is vital to building a robust vendor risk management framework.
Assessing Vendor Financial Stability
Evaluating a vendor's financial stability is a critical part of vendor risk assessment. This includes reviewing financial statements, credit ratings, and other relevant financial data. Analyzing a vendor's financial health helps to determine their ability to fulfill their contractual obligations and avoid potential financial distress.
Understanding a vendor's financial situation is crucial to making informed decisions about their suitability as a business partner. A financially unstable vendor could jeopardize the organization's operations and financial well-being.
Evaluating Vendor Compliance
Compliance with relevant regulations and standards is a critical aspect of vendor selection and ongoing management. This includes evaluating a vendor's adherence to industry standards, legal requirements, and internal policies. Non-compliance can lead to significant legal and reputational risks for the organization. Thorough review of compliance records and processes is crucial to avoid these risks.
Regular audits of vendor compliance are essential to ensure that they maintain their compliance throughout the duration of the relationship.
Implementing Mitigation Strategies
Once risks are identified and assessed, appropriate mitigation strategies must be implemented. These strategies may involve contractual provisions, performance monitoring, and other risk transfer mechanisms. Implementing these strategies can reduce the likelihood of negative impacts on the organization. Developing and implementing effective mitigation strategies is essential for minimizing the potential harm associated with vendor risks.
The specific mitigation strategies employed will vary depending on the nature and severity of the identified risks. A proactive approach to vendor risk management is crucial for avoiding costly disruptions and maintaining business continuity.
Ongoing Monitoring and Review
Vendor risk management is not a one-time activity; it's an ongoing process. Regular monitoring and review are essential to ensure that vendors continue to meet the organization's requirements. This includes tracking key performance indicators (KPIs), assessing compliance status, and evaluating any changes in the vendor's risk profile. Monitoring allows for proactive adjustments to mitigation strategies as circumstances evolve. Ongoing vigilance is crucial for maintaining a sound vendor risk management framework.
A robust vendor risk management program should include a process for regularly reviewing and updating vendor assessments and risk mitigation plans. This will ensure that the program remains relevant and effective over time.
Read more about Cybersecurity Frameworks for Protecting Supply Chain Intellectual Property
Hot Recommendations
- Offshore Wind for Industrial Power
- Agrivoltaics: Dual Land Use with Solar Energy Advancements: Sustainable Farming
- Hydrogen as an Energy Storage Medium: Production, Conversion, and Usage
- Utility Scale Battery Storage: Successful Project Case Studies
- The Role of Energy Storage in Grid Peak Shaving
- The Role of Startups in Renewable Energy
- The Role of Blockchain in Decentralization of Energy Generation
- The Future of Wind Energy Advancements in Design
- Synchronous Condensers and Grid Inertia in a Renewable Energy Grid
- Corporate Renewable Procurement for Government Agencies