How Blockchain is Shaping the Future of EV Security

Decentralization's Impact on Trust
In today's digital landscape, decentralized systems represent a paradigm shift in how we establish trust. By distributing control across multiple nodes rather than concentrating it in centralized authorities, these networks create a fundamentally different trust dynamic. Network participants interact through mathematically verifiable protocols rather than placing blind faith in institutions. This architectural approach doesn't eliminate trust - it redistributes it across cryptographic proofs and network consensus. The result is a system where manipulation requires compromising the majority of nodes simultaneously, creating inherent security through decentralization.
Immutable Records and Data Integrity
Blockchain's most revolutionary feature might be its ability to create permanent, unalterable records. Each transaction gets cryptographically sealed into blocks that reference previous entries, forming an indelible chain. This creates an unprecedented level of auditability - financial institutions can trace asset provenance, governments can maintain incorruptible public records, and supply chains can document every product movement. The implications extend beyond cryptocurrency; imagine medical records that patients can't accidentally alter or legal contracts that automatically enforce themselves through smart contracts.
Enhanced Security Through Cryptography
The security of decentralized systems stems from advanced cryptographic techniques working in concert. Hash functions convert data into unique digital fingerprints, while digital signatures verify transaction authenticity without revealing private keys. Elliptic curve cryptography provides robust security with relatively small key sizes, enabling efficient verification processes. These aren't theoretical protections - they're mathematical guarantees that have withstood decades of cryptanalysis. When properly implemented, they create systems where fraud becomes computationally infeasible rather than merely difficult.
Transparency and Accountability in Transactions
Public blockchains offer radical transparency by design - every transaction becomes permanently visible to all network participants. This creates powerful accountability mechanisms; while pseudonymous addresses protect user privacy, the complete transaction history remains auditable. For enterprise applications, permissioned blockchains can provide selective transparency where needed. This visibility transforms auditing processes, allowing regulators to monitor activity in real-time rather than relying on periodic reports. The transparency also enables innovative governance models where stakeholders can verify that rules are being followed.
The Role of Consensus Mechanisms
Consensus protocols represent the beating heart of decentralized networks. Proof-of-Work's energy-intensive computations secure Bitcoin by making attacks economically unfeasible. Proof-of-Stake alternatives like Ethereum's Casper protocol achieve security through financial stakes rather than computation. Emerging mechanisms like Proof-of-History or Directed Acyclic Graphs (DAGs) explore new approaches to distributed agreement. These aren't just technical details - they're carefully designed incentive structures that align participant behavior with network security. The right consensus model depends on the specific use case and desired tradeoffs between speed, security, and decentralization.
Scalability and Efficiency in Decentralized Networks
While early blockchain implementations faced legitimate scalability challenges, the ecosystem has responded with innovative solutions. Layer 2 protocols like Lightning Network process transactions off-chain while maintaining security guarantees. Sharding techniques parallelize transaction processing across network segments. New consensus algorithms dramatically reduce energy consumption compared to early Proof-of-Work systems. These advancements demonstrate that decentralization and performance aren't mutually exclusive - they simply require thoughtful architectural solutions. The ongoing evolution suggests decentralized systems will continue closing the gap with traditional databases.
Real-World Applications of Decentralized Trust
Beyond cryptocurrency speculation, blockchain enables tangible solutions across industries. Supply chains gain unprecedented visibility - consumers can verify organic cotton authenticity or conflict-free mineral sourcing. Healthcare systems can securely share patient records while maintaining strict access controls. Voting systems could leverage cryptography to prevent fraud while ensuring ballot secrecy. These applications demonstrate that decentralized trust isn't about replacing institutions, but about creating more verifiable, tamper-resistant systems where they're needed most. As the technology matures, we'll likely see even more creative applications emerge.
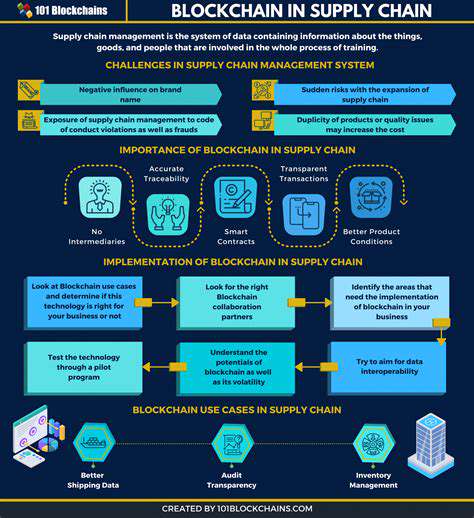
Enhanced Supply Chain Security with Blockchain
Strengthening Physical Security Measures
Modern supply chains require more than locks and cameras - they need intelligent security ecosystems. IoT sensors can monitor container conditions while in transit, detecting unauthorized openings or environmental changes. GPS tracking combined with geofencing creates digital perimeters that trigger alerts for deviations. Blockchain timestamps these events immutably, creating legally admissible evidence. This multi-layered approach transforms security from reactive to predictive, enabling interventions before losses occur. The data also helps optimize routes and identify recurring vulnerabilities in the supply network.
Improving Data Security and Transparency
Supply chain data often flows through vulnerable centralized databases prone to single points of failure. Blockchain distributes this data across nodes while encrypting sensitive information. Smart contracts can enforce data sharing rules - a supplier might see only relevant shipment details rather than the entire network. This granular control revolutionizes multi-party collaboration, allowing competitors to cooperate securely when needed. The technology also simplifies compliance by providing regulators with selective access to verified records without compromising trade secrets.
Implementing Robust Traceability Systems
From farm-to-table food tracking to pharmaceutical anti-counterfeiting, blockchain enables unprecedented product provenance. QR codes or NFC chips linked to immutable records let consumers verify authenticity with smartphone scans. For recalls, companies can pinpoint affected batches within minutes rather than days. This traceability creates powerful market differentiation - studies show consumers pay premiums for verifiably ethical or sustainable products. The technology also helps combat gray market diversion by creating digital ownership certificates that transfer with legitimate sales.
Developing Contingency Plans and Response Strategies
Blockchain-enabled supply chains can automatically trigger contingency protocols through smart contracts. A shipment delay might automatically reroute orders to alternate suppliers. Weather disruptions could initiate predefined insurance claims. These automated responses reduce human decision latency during crises. The shared ledger also improves coordination between disconnected parties - during port closures, all affected shippers can collaboratively optimize limited docking space based on verified priority claims recorded on-chain.
Securing Vehicle Data and Communication Channels
Protecting Vehicle Data from Cyber Threats
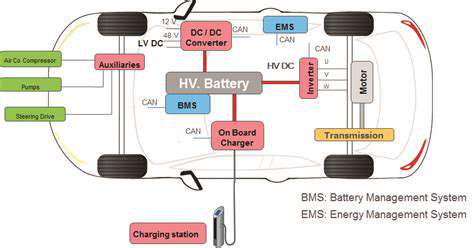
Modern vehicles contain over 100 million lines of code across dozens of interconnected systems - each a potential attack vector. Security must extend beyond traditional IT approaches to address automotive-specific threats like CAN bus injections or sensor spoofing. Hardware security modules (HSMs) provide tamper-resistant cryptographic operations for critical functions. Over-the-air updates must balance convenience with security, requiring cryptographic signatures and rollback protection. The stakes extend beyond data - researchers have demonstrated remote attacks that could disable brakes or steering at highway speeds.
Ensuring Data Integrity and Privacy
Vehicle data presents unique privacy challenges, capturing location histories, driving behaviors, and even cabin microphone recordings. Blockchain can help implement selective disclosure - proving insurance eligibility without revealing complete driving logs, for example. Zero-knowledge proofs allow verification of claims (like valid licenses) without exposing underlying data. These privacy-preserving techniques will become increasingly important as regulations like GDPR impose strict requirements on personal data collection and usage. Properly implemented, they can build consumer trust in connected vehicle technologies.
Developing Robust Security Protocols for Connected Features
Vehicle-to-everything (V2X) communication introduces complex security requirements. Messages about road conditions or emergency braking need both authentication and low latency. Blockchain can help manage the required public key infrastructure at scale while preventing certificate misuse. The solution lies in hybrid architectures - localized fast verification for time-critical functions, with periodic blockchain-anchored audits for accountability. As vehicles become mobile network nodes, these security frameworks will need to scale to millions of constantly moving endpoints.
Future Applications and Opportunities for Blockchain in EV Security
Enhanced Data Integrity and Transparency
Blockchain's tamper-evident ledgers could transform EV battery lifecycle management. Each charge cycle, temperature exposure, and performance metric could be immutably recorded, creating accurate battery health reports. This data becomes invaluable for second-life applications like grid storage - buyers could verify historical usage patterns. The same principle applies to charging infrastructure, where blockchain could prevent meter tampering while enabling innovative pricing models based on real-time grid demand.
Secure Supply Chain Management
EV components like lithium batteries involve complex global supply chains with ethical and environmental concerns. Blockchain can track cobalt from mine to manufacturer, ensuring conflict-free sourcing. Battery recycling programs could use digital tokens to incentivize proper disposal while preventing hazardous dumping. This traceability supports circular economy models where materials flow efficiently between production, use, and reuse phases with verified documentation at each step.
Improved Authentication and Identity Verification
Blockchain-based vehicle identity systems could prevent title washing and odometer fraud. Each maintenance event, ownership transfer, and accident report would permanently accumulate in the vehicle's digital twin. This creates a comprehensive vehicle history that's impossible to falsify, benefiting both buyers and insurers. The same technology could manage access rights - temporary digital keys for valets or repair shops that automatically expire after set periods.
Enhanced Cybersecurity Measures
As EVs become rolling computers, their attack surface grows exponentially. Blockchain can anchor firmware hashes, allowing vehicles to verify software integrity before installation. Anomaly detection systems could log suspicious activity on-chain, creating shared threat intelligence across manufacturers. This collaborative security model is essential as threats evolve faster than any single company can respond. The decentralized approach also prevents single points of failure that could affect entire fleets simultaneously.
Optimized Charging Infrastructure Management
Blockchain enables novel charging models like peer-to-peer energy trading between vehicles and homes. Smart contracts could automatically settle microtransactions for excess solar power shared between neighbors. Dynamic pricing could reflect real-time grid conditions while preventing manipulation. These systems require the auditability and automation that blockchain uniquely provides. The technology also simplifies roaming agreements between charging networks, allowing seamless cross-provider billing with reduced friction.
Facilitating Data-Driven Maintenance and Repair
By securely aggregating maintenance data across fleets, blockchain can power predictive analytics at scale. Anomalies detected in one vehicle could trigger proactive checks for others with similar usage patterns. Repair shops could access verified service histories while protecting owner privacy. This data liquidity benefits all stakeholders - manufacturers improve designs, insurers refine risk models, and owners enjoy longer vehicle lifespans through optimized maintenance.
Read more about How Blockchain is Shaping the Future of EV Security
Hot Recommendations
- Offshore Wind for Industrial Power
- Agrivoltaics: Dual Land Use with Solar Energy Advancements: Sustainable Farming
- Hydrogen as an Energy Storage Medium: Production, Conversion, and Usage
- Utility Scale Battery Storage: Successful Project Case Studies
- The Role of Energy Storage in Grid Peak Shaving
- The Role of Startups in Renewable Energy
- The Role of Blockchain in Decentralization of Energy Generation
- The Future of Wind Energy Advancements in Design
- Synchronous Condensers and Grid Inertia in a Renewable Energy Grid
- Corporate Renewable Procurement for Government Agencies