Edge Computing: Bringing Data Processing Closer to the Supply Chain
Securing Data and Enhancing Supply Chain Resilience
Data Security Measures
Robust data security measures are crucial for protecting sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. Implementing strong encryption protocols across all data transmission channels, coupled with regular security audits, helps mitigate risks. This proactive approach ensures the confidentiality, integrity, and availability of data assets, safeguarding valuable company information and maintaining trust with stakeholders. Furthermore, stringent access controls and user authentication mechanisms are essential elements of a comprehensive security strategy.
Regular security awareness training for employees is also vital. This training should cover topics such as phishing scams, social engineering tactics, and proper password management practices. Employees are often the weakest link in a security chain, and educating them about potential threats can significantly reduce the likelihood of successful attacks.
Supply Chain Resilience
A resilient supply chain is essential for maintaining operational continuity and minimizing disruptions. This involves diversifying sourcing strategies, building strong relationships with suppliers, and implementing contingency plans for potential disruptions. Proactively identifying and addressing vulnerabilities within the supply chain is paramount to mitigating risks and ensuring a stable and reliable flow of goods and services.
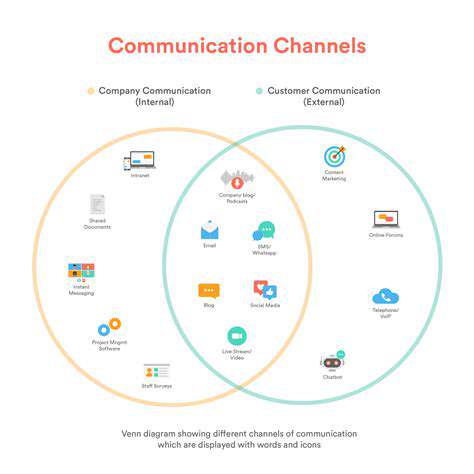
Establishing clear communication channels with suppliers and monitoring their performance helps to anticipate and address potential issues. This proactive approach helps to ensure that the supply chain remains robust and adaptable to changing market conditions.
Enhanced Transparency
Transparency in data handling and supply chain operations fosters trust and accountability. Implementing clear data governance policies, outlining data collection, storage, and usage practices, contributes to a more transparent and ethical approach to information management. Open communication regarding data security procedures and supply chain processes builds confidence among customers, partners, and employees. This fosters a collaborative environment that promotes trust and reduces potential conflicts.
Detailed documentation of supply chain processes, including materials sourcing, manufacturing, and distribution, provides an audit trail and ensures traceability. This visibility into the entire supply chain can help identify potential risks early on and allows for a more informed response to disruptions.
Strategic Partnerships
Strategic partnerships with reputable technology providers and security experts can significantly enhance data security and supply chain resilience. These partnerships can provide access to cutting-edge security technologies and expertise, allowing for a more proactive and comprehensive approach to risk management. Collaborating with industry leaders can lead to the adoption of best practices and innovative solutions, ultimately strengthening the overall security posture of the organization.
By leveraging the expertise of external partners, organizations can optimize their security infrastructure and gain a competitive advantage in the market. This approach helps to reduce the burden on internal resources and allows for a more focused approach to core business functions.
Read more about Edge Computing: Bringing Data Processing Closer to the Supply Chain
Hot Recommendations
- Offshore Wind for Industrial Power
- Agrivoltaics: Dual Land Use with Solar Energy Advancements: Sustainable Farming
- Hydrogen as an Energy Storage Medium: Production, Conversion, and Usage
- Utility Scale Battery Storage: Successful Project Case Studies
- The Role of Energy Storage in Grid Peak Shaving
- The Role of Startups in Renewable Energy
- The Role of Blockchain in Decentralization of Energy Generation
- The Future of Wind Energy Advancements in Design
- Synchronous Condensers and Grid Inertia in a Renewable Energy Grid
- Corporate Renewable Procurement for Government Agencies