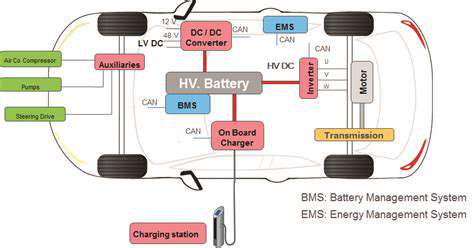
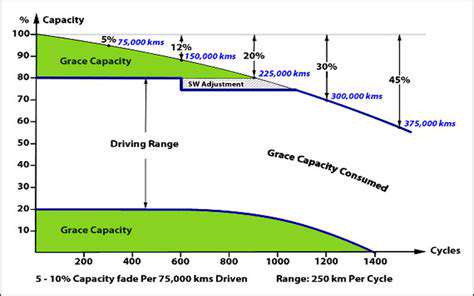
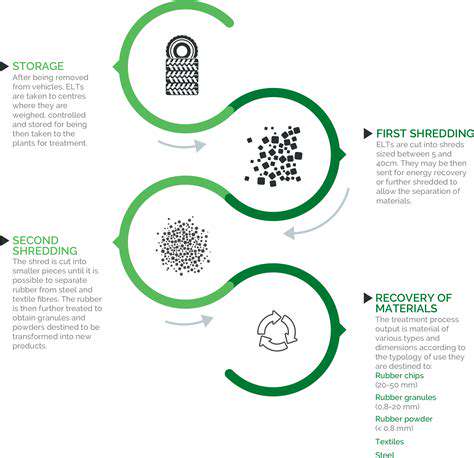
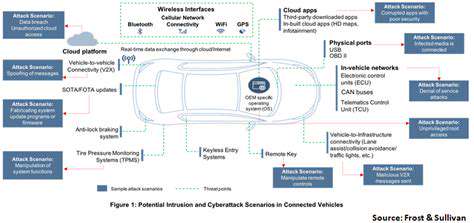
The Importance of Cybersecurity in Connected EVs
Addressing the Cybersecurity Challenges
While concerning, these cybersecurity threats aren't insurmountable. Automakers must implement multi-layered security measures starting from the initial design phase. This includes military-grade encryption protocols and biometric authentication systems. Regular penetration testing by ethical hackers helps identify vulnerabilities before criminals can exploit them.
The cybersecurity battle requires constant vigilance. Manufacturers must establish rapid-response teams to deploy security patches the moment new threats emerge. Simultaneously, consumer education plays a critical role. Drivers should understand basic protective measures like avoiding public WiFi for vehicle updates and recognizing phishing attempts disguised as service notifications.
True security demands industry-wide cooperation. Automakers, cybersecurity firms, and government regulators must collaborate to establish universal safety standards. This collective approach should incorporate cutting-edge solutions like AI-powered intrusion detection systems that learn and adapt to new attack methods in real-time. The future of EV adoption depends on public confidence in these security measures.
The Crucial Role of Secure Software Development Lifecycle (SDLC)
Defining Secure SDLC
A Secure Software Development Lifecycle represents a paradigm shift in how we build automotive software. Unlike traditional methods that treat security as an afterthought, this approach weaves protective measures into every development phase. This cultural transformation makes security everyone's responsibility rather than just the cybersecurity team's concern.
Security in Requirements Gathering
The foundation of secure software begins with threat modeling during initial planning. Development teams must anticipate every conceivable attack vector - from brute force login attempts to sophisticated supply chain compromises. By documenting these risks early, engineers can design appropriate safeguards directly into the system architecture.
Secure Design and Architecture
Modern EV software requires a defense-in-depth architecture. This means implementing multiple security layers so if one fails, others remain intact. Critical components should operate in isolated environments with strict access controls. All data transmissions must use end-to-end encryption with regularly rotated cryptographic keys.
Implementing Secure Coding Practices
Human error remains the weakest link in software security. Development teams need ongoing training in secure coding techniques. Automated tools should scan every code commit for common vulnerabilities like buffer overflows or SQL injection possibilities. Peer code reviews provide additional oversight to catch potential issues.
Thorough Testing and Validation
Security testing must evolve beyond simple functionality checks. Ethical hacking teams should attempt to breach systems using the same tools and techniques as actual cybercriminals. Fuzz testing bombards software with random inputs to uncover hidden vulnerabilities. These tests should occur throughout development, not just before release.
Security in Deployment and Maintenance
The work doesn't stop at deployment. Continuous monitoring systems must watch for anomalous behavior that could indicate a breach. Over-the-air update mechanisms require bulletproof security to prevent hackers from disguising malware as legitimate updates. Regular third-party audits ensure no security degradation over time.
The Importance of Industry Collaboration and Regulation

Collaborative Innovation
When industry leaders combine forces, they create an innovation powerhouse. This collaborative energy often achieves breakthroughs that would take individual companies years to accomplish alone. Shared testing facilities and research databases accelerate development cycles while reducing redundant efforts across the industry.
Enhanced Market Reach and Competitive Advantage
Strategic partnerships provide access to new customer segments through combined distribution networks. More importantly, they enable companies to pool market intelligence, creating products that better address real consumer needs. This customer-centric approach delivers superior products while minimizing costly development missteps.
Shared Risks and Reduced Costs
Collaboration transforms high-risk projects into manageable ventures. By sharing R&D expenses, companies can pursue ambitious technologies like solid-state batteries or autonomous driving systems. Joint purchasing agreements for components yield significant cost savings that benefit both manufacturers and consumers.
Improved Efficiency and Productivity
The cross-pollination of best practices between partners leads to remarkable efficiency gains. Manufacturing processes improve as companies share lean production techniques. Supply chain optimizations developed by one partner often benefit the entire collaboration network.
Building Trust and Strengthening Relationships
Successful collaborations create bonds that extend beyond individual projects. The trust built through shared successes leads to faster decision-making in future ventures. These relationships become particularly valuable during industry disruptions, providing stability through challenging transitions.